How secure is Wonga.com?
Over the weekend money lender Wonga.com announced it has suffered a large data breach that could affect up to 270,000 UK customers.
The data stolen includes personal information such as names, addresses, phone numbers and bank details like sort codes/account numbers etc.
To it’s credit they have setup an incident page (https://www.wonga.com/help/incident-faq) on their site and made the link to it very clear from their homepage.
How were they breached
They haven’t announced how the breach happened, but they have stated:
“Cyber attacks are, unfortunately, on the rise. While Wonga operates to the highest security standards, these illegal attacks are unfortunately increasingly sophisticated.”
They are hinting that it was a highly sophisticated attack and given the impression there was not much they could have done about it. This sounds similar to the noises TalkTalk were making a while back which ended up being SQL Injection – not exactly the most sophisticated type of attack and has been known about for years.
It looks like Wonga.com is now running behind a web application firewall which is good however there is something that could point to their security not being quite as good as they’re claiming.
Here’s a screenshot from securityheaders.io:
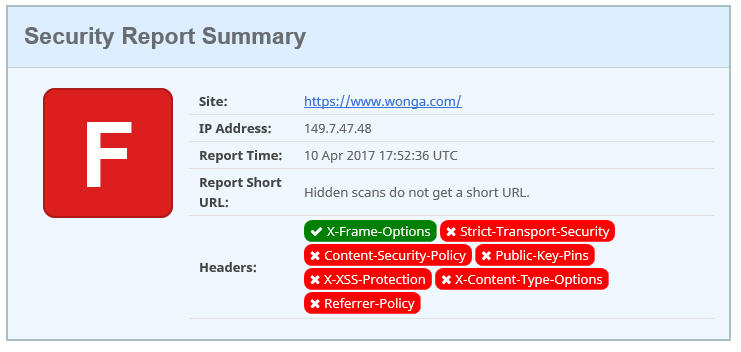
The site scores an F grade as it’s not setting recommended security headers such as HSTS etc. However more interestingly they have few headers which would often be turned off once the server has been setup, this tells anyone looking what software (and version numbers) the website is running on.
Server: nginx/1.4.6 (Ubuntu)
X-Powered-By: PHP/5.6.30-7+deb.sury.org~trusty+1
X-Drupal-Cache: MISS
These headers would often be flagged up in an external penetration test/audit as it gives the attacker information that could be used to help speed up the process of exploiting the site.
It is a little concerning that either these relatively simple things to change from there default settings haven’t been done or haven’t been picked up in a security review.
It’s possible (but unlikely) that they’re faking the header information to misdirect people.