Digispark USB Development Board
The technical description of the Digispark is that is an Attiny85 based microcontroller development board similar to the Adruino boards but cheaper, smaller and slightly less powerful.
The less technical description is that it’s a small USB device that you can program to be anything you want it to be. It’s fantastic for anyone getting into electronics due to it’s simplicity as you can upload your code to it via USB rather than needing an extra bit of hardware (a programmer) and a pack of 3 can be bought on ebay for £5.62 including shipping!
The Devious Part
The Digispark can be programmed so that it gets recognised as a human input device (HID) such as keyboards, mice etc. This opens up the opportunity to inject keystrokes onto the host without actually touching the keyboard, you need to remember that everything on the screen is still visible so you would need roughly 5 to 15 seconds from the moment you connect the USB to distract your target or for them to be out of the room. In that time the device could have entered enough keystrokes to download a reverse shell and executed on the host.
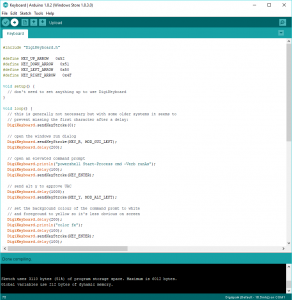
Above: A screenshot of the Arduino IDE used to program the Digispark.
There are so many opportunities in the real world to execute a hack like this, in the last two weeks I’ve counted the following:
- A laptop for festival events company left unlocked on a quiet train while the owner went to the toilet.
- A customer service employee for a high profile bank left a meeting room to fetch a glass of water leaving me with her laptop unlocked for a few minutes.
- A PC at a meetup.com group (hosted at a big software firm), although this may have been slightly more risky.
- The managers PC at a carehome, it was locked but there full unattended access to attach the device.
If you wanted to do something a little less obvious you could run any command you wanted like sharing the whole of the c:\ drive with everyone, then connect later via another network device to steel content/emails from your target.
Mitigation Tactics
Short of filling the physical USB sockets with concrete this can be hard to defend against as the USB device is recognised as a keyboard rather than something malicious.
Good staff training helps, making them aware of the risks and a policy of never leaving PCs unattended while unlocked and ensuring guests are never left alone even for a short while.
A game I started amongst some of the staff was to set the background image to a random picture of Bruce Forsyth if a PC was left unlocked without the user of the PC spotting it being done. Ok I know that’s sounds very childish (and it is) but it was so much more effective than anything else and it soon became second nature to everyone to lock their machine even if turning away for a moment.